https://buuoj.cn/challenges#[GWCTF%202019]re3
elf 64
IDA 动调加密的函数出来是
void __fastcall __noreturn main(int a1, char **a2, char **a3)
{
int i; // [rsp+8h] [rbp-48h]
char input[40]; // [rsp+20h] [rbp-30h] BYREF
unsigned __int64 v5; // [rsp+48h] [rbp-8h]
v5 = __readfsqword(0x28u);
__isoc99_scanf("%39s", input);
if ( (unsigned int)strlen(input) != 32 )
{
puts("Wrong!");
exit(0);
}
mprotect(&dword_400000, 0xF000uLL, 7);
for ( i = 0; i <= 223; ++i )
*((_BYTE *)sub_402219 + i) ^= 0x99u;
sub_40207B(buff);
sub_402219();
}
unsigned __int64 __fastcall sub_40207B(char *buff)
{
char v2[16]; // [rsp+10h] [rbp-50h] BYREF
__int64 v3; // [rsp+20h] [rbp-40h] BYREF
__int64 v4; // [rsp+30h] [rbp-30h] BYREF
__int64 v5; // [rsp+40h] [rbp-20h] BYREF
unsigned __int64 v6; // [rsp+58h] [rbp-8h]
v6 = __readfsqword(0x28u);
md5(&BASE64_table_603120, 64LL, v2);
md5(&unk_603100, 20LL, &v3);
md5(&Prime_Constants_char_6030C0, 53LL, &v4);
md5(&MD5_Constants_4025C0, 256LL, &v5);
md5(v2, 64LL, buff);
return __readfsqword(0x28u) ^ v6;
}
__int64 __fastcall sub_40221A(__int64 a1)
{
unsigned int v2; // [rsp+18h] [rbp-D8h]
int i; // [rsp+1Ch] [rbp-D4h]
char v4[200]; // [rsp+20h] [rbp-D0h] BYREF
unsigned __int64 v5; // [rsp+E8h] [rbp-8h]
v5 = __readfsqword(0x28u);
sub_400A71((__int64)v4, (__int64)&buff);
sub_40196E(v4, a1);
sub_40196E(v4, a1 + 16);
v2 = 1;
for ( i = 0; i <= 31; ++i )
{
if ( *(_BYTE *)(i + a1) != byte_6030A0[i] )
v2 = 0;
}
return v2;
}
__int64 __fastcall sub_40196E(__int64 a1, __int64 a2)
{
return sub_401828(a2, a1);
}
__int64 __fastcall sub_401828(__int64 a1, __int64 a2)
{
unsigned __int8 i; // [rsp+1Fh] [rbp-1h]
sub_400B0A(0LL, a1, a2);
for ( i = 1; i <= 9u; ++i )
{
sub_400BAC(a1);//AES
sub_400C1F(a1);
sub_400D27(a1);
sub_400B0A(i, a1, a2);
}
sub_400BAC(a1);
sub_400C1F(a1);
return sub_400B0A(10LL, a1, a2);
}是一个判断
插件识别常量发现一坨加密……
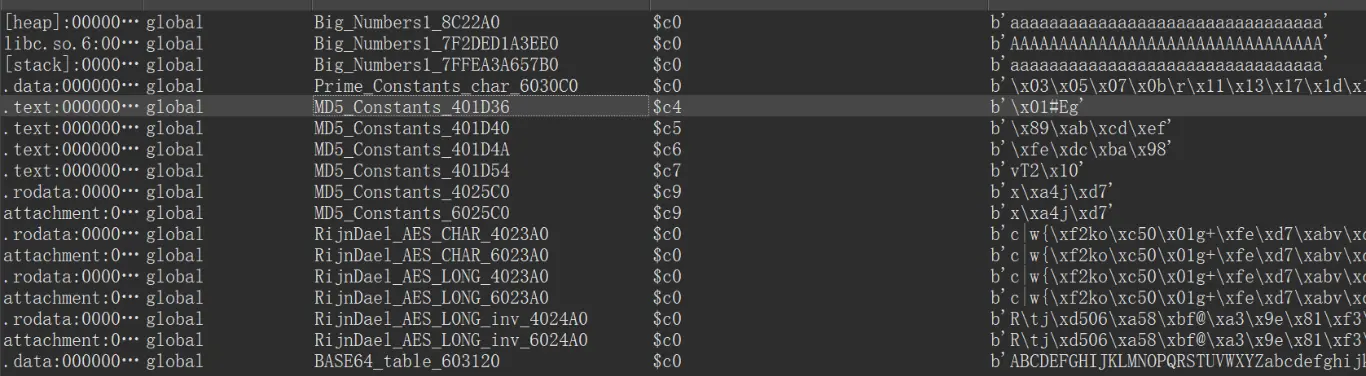
其实只用看对输入做处理的函数 sub_40221A 就可以了
sub_400A71((__int64)v4, (__int64)&buff); 把 buff 加密到 v4 中
sub_40196E(v4, a1);sub_40196E(v4, a1 + 16); 把 a1 用 v4 aes 加密了
之后再比较加密结果
这样用 cyberchef 逆回去就很方便
export data 出来 key:16
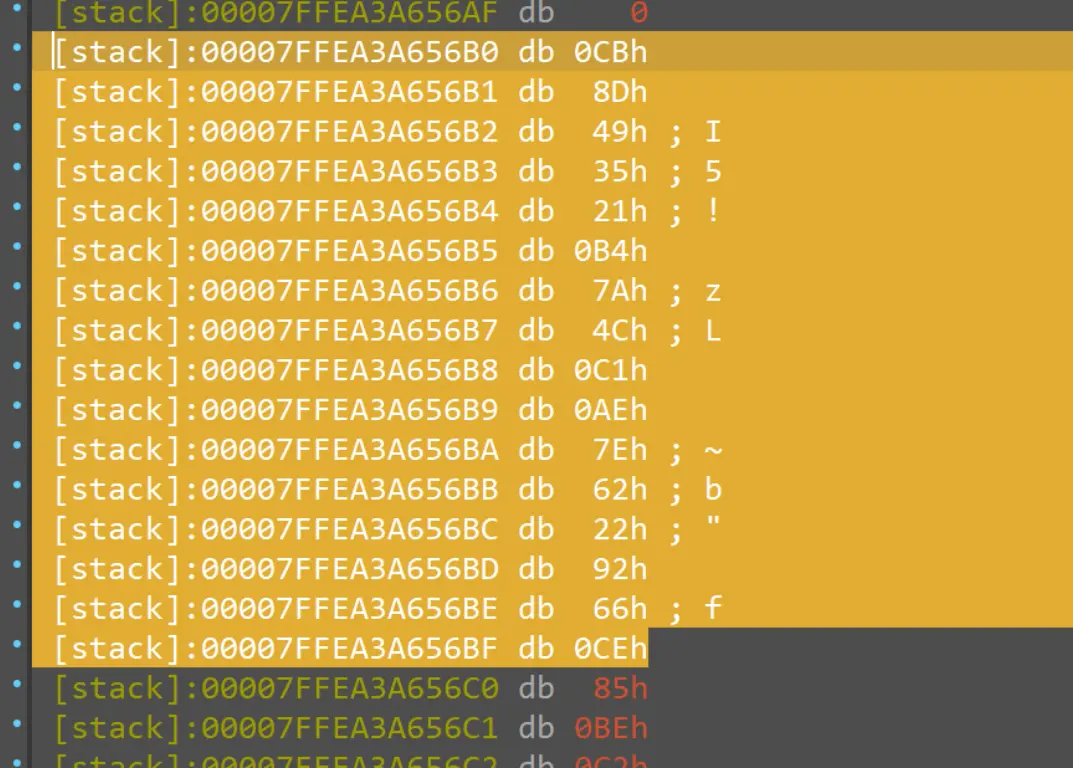
CB8D493521B47A4CC1AE7E62229266CE
密文:
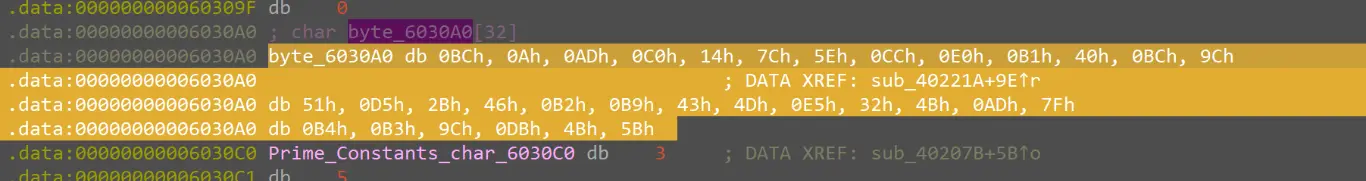
BC0AADC0147C5ECCE0B140BC9C51D52B46B2B9434DE5324BAD7FB4B39CDB4B5B
选择 ECB-NoPadding 解密 得到 flag
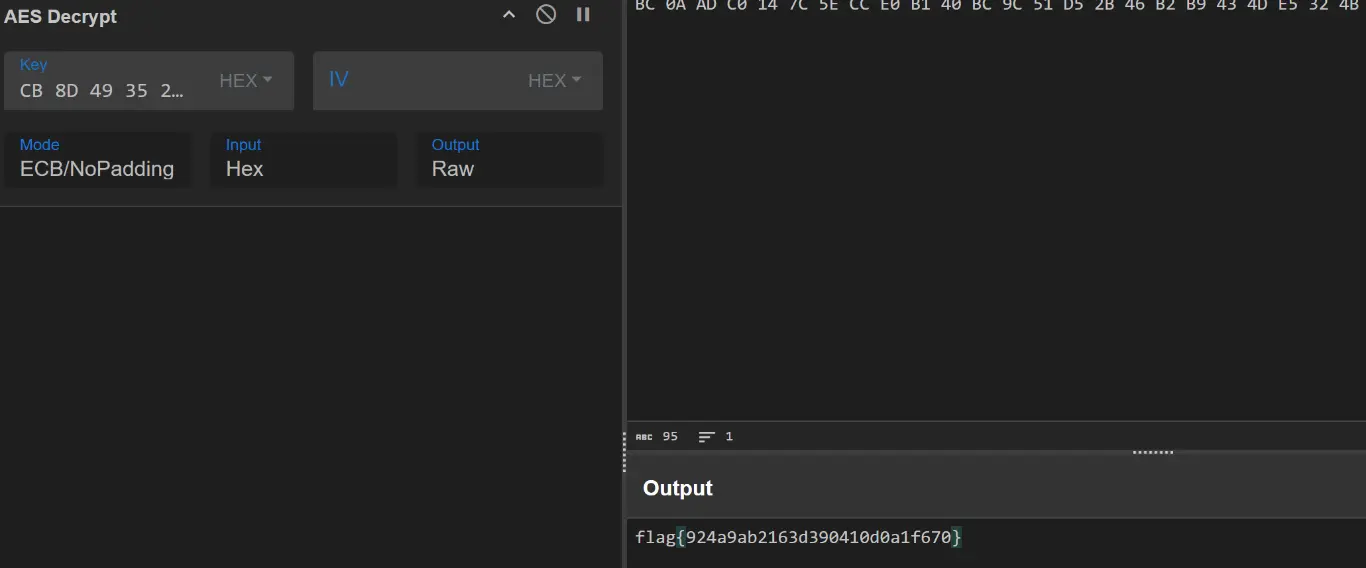
flag{924a9ab2163d390410d0a1f670}