https://bbs.kanxue.com/thread-267670.htm
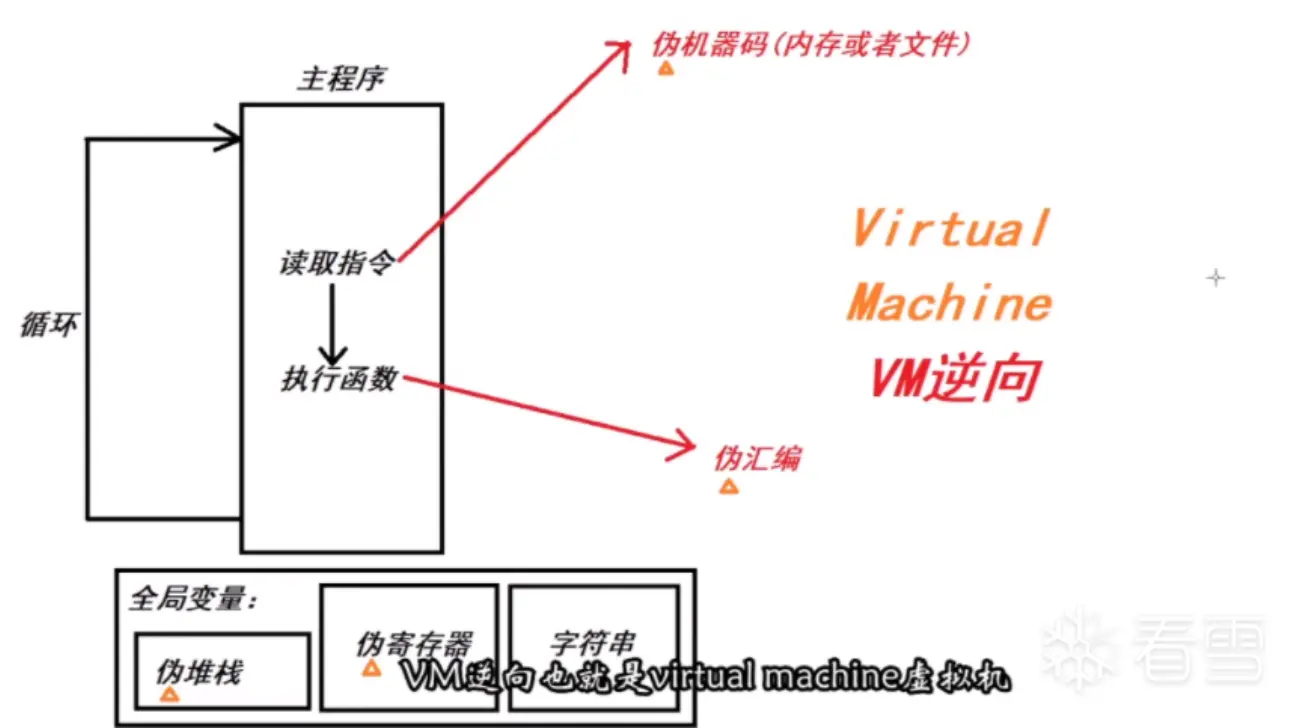
全局变量中的堆栈、寄存器和字符串共同构成了内存 +CPU 寄存器
先查找到 opcode(伪机器码),然后找到 dispatcher(就是模拟 CPU 读取指令的分发器),然后边分析那些伪汇编函数 (就是模仿汇编指令的函数) 边查找模拟的 CPU 的栈,寄存器,全局变量 (多是字符串) 等
- vm_nop
- vm_push_data
- vm_push_reg
- vm_pop_reg
- vm_printf
- vm_add_reg_reg1
- vm_sub_reg_reg1
- vm_mul
- vm_div
- vm_xor
- vm_jmp
- vm_cmp
- vm_je
- vm_jne
- vm_jg
- vm_jl
- vm_scanf_strlen
- vm_mem_init
- stack_to_reg
- load_input
- vm_exit
招新赛:
opcode = [1, 3, 0, 2, 0, 3, 1, 1, 35, 17,
0, 1, 1, 1, 17, 10, 0, 1, 3, 1,
3, 8, 0, 1, 9, 0, 43, 1, 1, 1,
10, 3, 1, 1, 1, 28, 6, 3, 1, 9,
1, 3, 18, 19, 0,]
data = [81, 94, 97, 97, 105, 120, 93, 94, 31, 104,
141, 135, 39, 87, 141, 134, 130, 141, 35, 126,
141, 37, 93, 91, 96, 87, 37, 111]
opcode_key = {
1: 'mov r{}, {}',
2: 'mov r{}, [flag+r{}]',
3: 'mov r{}, [data+r{}]',
4: 'le r{}, r{}', # flag 在 r2
5: 'ge r{}, r{}',
6: 'l r{}, r{}',
7: 'g r{}, r{}',
8: 'eq {}, r{}',
9: 'je r{}, {}', # cmp 对象在 r2
10: 'add r{}, r{}',
11: 'sub r{}, r{}',
12: 'mul r{}, r{}',
13: 'div r{}, r{}',
14: 'mod r{}, r{}',
15: 'or r{}, r{}',
16: 'and r{}, r{}',
17: 'xor r{}, r{}',
18: 'return 1',
19: 'return 0',
}
for i in range(0, len(opcode), 3):
op0 = opcode[i]
op1 = opcode[i+1]
op2 = opcode[i+2]
print('#'+f'{i}'.rjust(3)+f' {opcode_key[op0].format(op1, op2)}')
print("# 43 return 0")
for i in range(len(data)):
data[i]=(data[i]-17)^35
print("".join([chr(i) for i in data]))
# 0 mov r3, 0
# 3 mov r0, [flag+r3]
# 6 mov r1, 35
# 9 xor r0, r1
# 12 mov r1, 17
# 15 add r0, r1
# 18 mov r1, [data+r3]
# 21 eq 0, r1
# 24 je r0, 43
# 27 mov r1, 1
# 30 add r3, r1
# 33 mov r1, 28
# 36 l r3, r1
# 39 je r1, 3
# 42 return 1
# 43 return 0